The cybersecurity frameworks

The cyber threat landscape is rapidly changing, with advanced persistent threats, state-sponsored attacks, and sophisticated phishing schemes. The rise of IoT and remote work has expanded vulnerabilities, making robust cybersecurity measures and continuous vigilance more crucial than ever to protect data and maintain privacy in an increasingly connected world.
Proactive cybersecurity measures are essential to thwart attacks before they occur. By anticipating threats, implementing robust defenses, and continuously monitoring systems, organizations can prevent data breaches, protect sensitive information, and maintain trust. Being proactive not only mitigates risks but also minimizes potential financial and reputational damage from cyber incidents.
The Cybersecurity Framework Implementation project aims to integrate comprehensive security protocols across an organization’s digital landscape. By adopting a structured framework, it ensures consistent application of best practices, strengthens defense mechanisms, and enhances resilience against cyber threats, ultimately safeguarding assets and maintaining operational integrity in the face of evolving cyber risks.
The cybersecurity frameworks implementation process
Phase 1: Policy and Framework Alignment
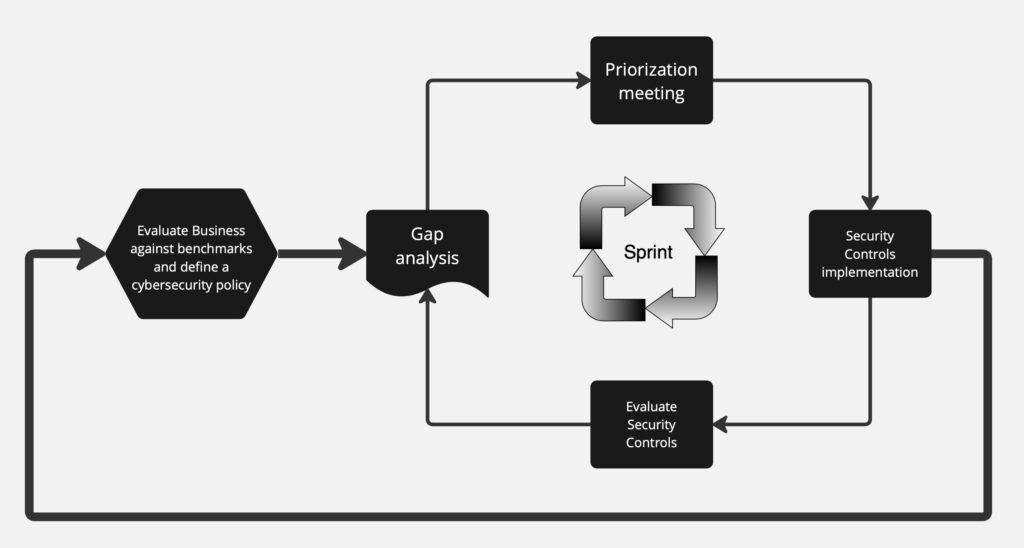
Assess current cybersecurity practices against industry frameworks (e.g., NIST).
Define a tailored cybersecurity policy aligned with business objectives and regulations.
-
- Evaluation of the actual cybersecurity status of the busineess through interviews and automated tools;
-
- Look from the availables fameworks and best practices what does apply to the business and eventually merging then.
-
- Based on the previous work we plan our goals.
Phase 2: Gap Analysis and Prioritization
Conduct a detailed gap analysis based on the established policy.
Prioritize critical issues posing significant risk to the business.
-
- Risk assessment is a critical process that evaluates the severity and likelihood of potential threats, enabling organizations to prioritize resources and implement appropriate security measures.
-
- Identifying discrepancies between current practices and policy is crucial for compliance and security. It involves scrutinizing operational procedures against established guidelines to uncover gaps.
-
- Prioritizing critical gaps based on risk and business impact is essential for effective cybersecurity management. By assessing the potential damage and likelihood of threats, organizations can allocate resources strategically to address the most pressing vulnerabilities, thereby minimizing risk exposure and safeguarding key assets against disruptive cyber incidents.
Phase 4: Continuous Improvement
Monthly gap analysis revisit to identify and address new vulnerabilities.
Annual business reevaluation to adapt to evolving threats and changes.
-
- Testing and evaluating implemented controls ensures their effectiveness in mitigating cyber threats.
-
- Identifying gaps or inefficiencies is critical for enhancing control performance.
-
- Continuous monitoring and refinement of security controls are imperative for maintaining a robust cybersecurity posture, adapting to new threats, and protecting organizational assets in a dynamic digital environment.
Phase 3: Security Control Implementation
Implement prioritized security controls following best practices and policy compliance.
Evaluate and monitor the effectiveness of implemented controls.
Phase 1: Policy and Framework Alignment
Assess current cybersecurity practices against industry frameworks (e.g., NIST).
Define a tailored cybersecurity policy aligned with business objectives and regulations.
-
- Evaluation of the actual cybersecurity status of the busineess through interviews and automated tools;
-
- Look from the availables fameworks and best practices what does apply to the business and eventually merging then.
-
- Based on the previous work we plan our goals.
Phase 2: Gap Analysis and Prioritization
Conduct a detailed gap analysis based on the established policy.
Prioritize critical issues posing significant risk to the business.
-
- Risk assessment is a critical process that evaluates the severity and likelihood of potential threats, enabling organizations to prioritize resources and implement appropriate security measures.
-
- Identifying discrepancies between current practices and policy is crucial for compliance and security. It involves scrutinizing operational procedures against established guidelines to uncover gaps.
-
- Prioritizing critical gaps based on risk and business impact is essential for effective cybersecurity management. By assessing the potential damage and likelihood of threats, organizations can allocate resources strategically to address the most pressing vulnerabilities, thereby minimizing risk exposure and safeguarding key assets against disruptive cyber incidents.
Phase 3: Security Control Implementation
Implement prioritized security controls following best practices and policy compliance.
Evaluate and monitor the effectiveness of implemented controls.
Phase 4: Continuous Improvement
Monthly gap analysis revisit to identify and address new vulnerabilities.
Annual business reevaluation to adapt to evolving threats and changes.
-
- Testing and evaluating implemented controls ensures their effectiveness in mitigating cyber threats.
-
- Identifying gaps or inefficiencies is critical for enhancing control performance.
-
- Continuous monitoring and refinement of security controls are imperative for maintaining a robust cybersecurity posture, adapting to new threats, and protecting organizational assets in a dynamic digital environment.
